In this blog post, we take an in-depth look at the world of side-channel attacks.
We describe how side-channel attacks work and detail some of the most common attack methodologies. We also explore differential power analysis (DPA), an extremely powerful side-channel attack capable of obtaining and analyzing statistical measurements across multiple operations. In addition, we provide a walkthrough of a DPA attack and explain how different countermeasures with varying levels of effectiveness can be used to prevent side-channel attacks.
Table of contents
- What is a side-channel attack?
- How does a side channel attack work?
- What attacks use side channel analysis?
- DPA explained
- DPA & Paul Kocher
- Technical example of a differential power analysis attack
- Countermeasures: Preventing Side-channel attacks
- Final thoughts
What is a side-channel attack?
A side-channel attack (SCA) is a security exploit that attempts to extract secrets from a chip or a system. This can be achieved by measuring or analyzing various physical parameters. Examples include supply current, execution time, and electromagnetic emission. These attacks pose a serious threat to modules that integrate cryptographic systems. Indeed, many side-channel analysis techniques have proven successful in breaking an algorithmically robust cryptographic operation and extracting the secret key.
How does a side channel attack work?
A side-channel attack does not target a program or its code directly. Rather, a side-channel attack attempts to gather information or influence the program execution of a system by measuring or exploiting indirect effects of the system or its hardware. Put simply, a side channel attack breaks cryptography by exploiting information inadvertently leaked by a system. One such example is van Eck phreaking attack, which is also known as a Transient Electromagnetic Pulse Emanation Standard (TEMPEST). This attack monitors the electromagnetic field (EMF) radiation emitted by a computer screen to view information before it is encrypted.
What attacks use side channel analysis?
There are a growing number of known side-channel attack vectors. Some of the most common attacks are:
- Timing attack: Analyzes the time a system spends executing cryptographic algorithms. Keep on reading: Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems »
- Electromagnetic (EM) attack: Measures and performs a signal analysis on the electromagnetic radiation emitted from a device.
- Simple power analysis (SPA): Directly observes the power and electromagnetic (EM) variations of a cryptographic system during operations.
- Differential power analysis (DPA): Obtains and analyzes detailed statistical measurements across multiple operations.
- Template attack: Recovers cryptographic keys by exploiting an identical “template” device and comparing side-channel data.
DPA explained: Why is this black-box attack considered one of the most efficient and dangerous attacks?
- Definition: A Differential Power Analysis (DPA) is a form of side-channel attack that monitors variations in the electrical power consumption or electro-magnetic emissions of a target device. The basic method involves partitioning a set of traces into subsets, then subsequently computing the difference of the averages of these subsets.
- Differences: DPA is an extremely powerful technique that obtains and analyzes statistical measurements across multiple operations.
- What makes DPA more efficient/dangerous? Given enough traces, extremely minute correlations can be isolated—no matter how much noise is present in the measurements. DPA can even extract information about individual gate-switching, an individual transistor turning on or off, or the interaction between one gate and another.
DPA & Paul Kocher: An introduction to differential power analysis
How does an attacker target a device or system using DPA? In the paper titled “Introduction to Differential Power Analysis,” Paul Kocher describes how information inadvertently leaked through power consumption and other side channels can be analyzed to extract secret keys from a wide range of devices.
The attacks are practical, non-invasive, and highly effective—even against complex and noisy systems where cryptographic computations account for only a small fraction of the overall power consumption.
Technical example of a differential power analysis attack
The following steps detail the DPA attack process.
1. Make power consumption measurements of the last few rounds of 1000 DES operations. Each sample set consists of 100000 data points. The data collected can be represented as a two-dimensional array S[0…999][0…99999], where the first index is the operation number and the second index is the sample. For this example, the attacker is also assumed to have the encrypted ciphertexts, C[0…999].
2. The attacker next chooses a key-dependent selection function D. In this case, the selection function would have the form D(Ki,C), where Ki is some key information and C is a ciphertext.
For example, the attacker’s goal will be to find the 6 bits of the DES key that are provided as the input to the DES S box 4, so Ki is a 6-bit input. The result of D(Ki,C) would be obtained by performing the DES initial permutation (IP) on C to obtain R and L, performing the E expansion on R, extracting the 6-bit input to S4, XORing with Ki, and using the XOR result as the input to the standard DES S4 lookup operation.
A target bit (for example, the most significant bit) of the S result is selected. The P permutation is applied to the bit. The result of the D(Ki,C) function is set to 0 if the single-bit P permutation result and the corresponding bit in L are equal, and otherwise D(Ki,C) yields 1.
3. A differential average trace T[0…63][0…99999] is constructed from the data set S using the results of the function D. In particular:
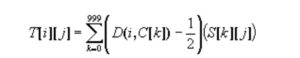
4. The attacker knows that there is one correct value for Ki; other values are incorrect. The attack goal is to identify the correct value. In the trace T[i][0…99999] where i=Ki, D(i,C[k]) for any k will equal the value of the target bit in L of the DES operation before the DES F function result was XORed. When the target device performed the DES operations, this bit value was stored in registers, manipulated in logic units, etc. — yielding detectable power consumption differences.
Thus, for the portions of the trace T[i=Ki] where that bit was present and/or manipulated, the sample set T[i] will show power consumption biases. However, for samples T[i != Ki], the value of D(i,C[k]) will not correspond to any operation actually computed by the target device. As a result, the trace T[i] will not be correlated to anything actually performed, and will average to zero. (Actually, T[i != Ki] will show small fluctuations due to noise and error that is not statistically filtered out, and due to biases resulting from statistical properties of the S tables. However, the largest biases will correspond to the correct value of Ki.)
5. The steps above are then repeated for the remaining S boxes to find the 48 key bits for the last round. The attack can then be repeated to find the previous round’s subkey (or the remaining 8 bits can be found using a quick search).
Countermeasures: Preventing Side-channel attacks
Countermeasures fall into two main categories:
Category 1: Eliminate or reduce the release of such information.
Countermeasures for category 1
- Jam the emitted channel with noise: Specifically, random delays are introduced to deter timing attacks. The arbitrary and artificial “noise” forces an adversary to collect more measurements. It should be noted that standalone noise introduction is incapable of sufficiently masking side-channel emissions. DPA conducted against a device can effectively bypass stand-alone noise countermeasures, ultimately allowing the signal to be isolated.
- Apply power line conditioning and filtering: Although somewhat effective, this method may not eliminate all minute correlations—and could potentially allow a determined attacker to compromise system security.
- Analyze and evaluate: All electronic systems should be carefully evaluated with a Test Vector Leakage Assessment (TVLA) platform such as the Rambus DPA Workstation (DPAWS) to identify sensitive side-channel leakage.
- Implement a silicon-based hardware root of trust: Rambus DPA Resistant hardware cores (DPARC)—which feature integrated countermeasures—are built around optimized implementations of industry accepted ciphers such as AES, SHA-256, RSA and ECC. These countermeasures have been designed and extensively validated using the Test Vector Leakage Assessment (TVLA) methodology revealing no leakage beyond 100 million traces, which means the cores are protected against univariate first and second-order side-channel attacks beyond 1 billion operations.
Category 2: eliminate the relationship between the leaked information and the secret data.
Countermeasures for category 2
- Apply blinding techniques: This technique alters the algorithm’s input (for asymmetric encryption schemes) into an unpredictable state to prevent leakage.
- Implement masking: This countermeasure randomly splits every sensitive intermediate variable occurring in the computation into d + 1 shares. Although widely used in practice, masking is often considered as an empirical solution and its effectiveness is rarely proved.
Final thoughts
Side-channel attacks conducted against electronic equipment and infrastructure are relatively simple and inexpensive to execute. An attacker does not necessarily need to know specific implementation details of the cryptographic device to perform these attacks and extract keys. Side-channel attacks have successfully cracked the hardware or software implementations of numerous cryptosystems including block ciphers such as DES, AES, Camellia, IDEA and Misty1. Side-channel attacks have also broken stream ciphers (RC4, RC6, A5/1 and SOBER-t32) and public key ciphers. Since all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.
Here at Rambus, we developed fundamental solutions and techniques for protecting devices against DPA and related side-channel attacks, along with supporting tools, programs, and services. Learn more about our DPA Countermeasure solutions.
Explore more primers:
– Hardware root of trust: All you need to know
– PCI Express 5 vs. 4: What’s New?
– DDR5 vs DDR4 – All the Design Challenges & Advantages
– Compute express link: All you need to know
– MACsec Explained: From A to Z
– The Ultimate Guide to HBM2E Implementation & Selection
Read more about “Side-channel attacks” topic:
The importance of protecting military equipment from side-channel attacks
Detecting and analyzing side-channel vulnerabilities with TVLA
TEMPEST side-channel attacks recover AES-256 encryption keys


Leave a Reply