It used to be that identifying and addressing potential side channel attack risks in semiconductor devices like SoCs was a lengthy process and highly cumbersome. But thanks to the Rambus DPAWS 9.0 , that troublesome, time consuming, and prototype lab environment type of testing is a thing of the past.
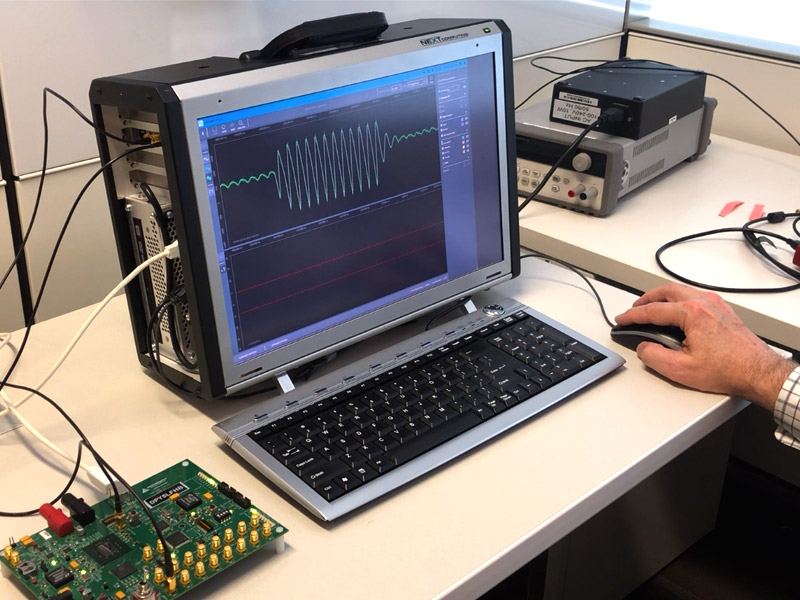
Today, the Differential Power Analysis WorkStation 9.0 (or DPAWS 9.0) is bringing a point and click user experience to test and security engineers at semiconductor and defense companies. The DPAWS 9.0 system allows those engineering staffs to assess differential power analysis (DPA) and fault injection attack (FIA) resistance to chips under test.
Previously, side channel attack testing was a long, cumbersome exercise in custom-built command line code, typically only performed by highly trained, experienced engineers. Today, DPAWS 9.0 offers a Windows-based user interface that allows test and security engineers, efficient, quick and easy operational use. Pre-loaded code allows them to automatically run one or more tests as opposed to running a large amount of command line code. A test or security engineer simply clicks on the selected test and hits the “execute” key.
Avoid Custom Script
Without having to write custom script, the engineering user achieves immediate results in a considerably more efficient manner by not going through dozens of command line interfaces. The point and click top feature of DPAWS 9.0 provides instant feedback on testing.
If there are failures, those are immediately seen since there is a visualizer built into the test platform. Before, test and security engineering had to wait until the end of the testing process, collect all the raw data, and then run that raw data to understand whether or not a chip under test was leaking or not. However, with the built-in DPAWS 9.0 visualizer, test and security engineers see results in real time.
In instances where DPAWS 9.0 indicates the chip under test has a low resistance to DPA, Rambus offers users DPA software libraries (DPASL), which can be added to in-production silicon if enough memory is on that particular chip.
Or, chipmakers have the option of embedding DPA resistant hardware cores (DPARC) in their chips. These are easy-to-integrate technology-independent soft-macro security solutions with built-in side-channel resistance for cryptographic functions across a wide array of devices. As part of a chip’s design, these DPA cores expand security safety to a certain number of operations. Some DPA cores are resistant to 100 million traces; others are resistant to a billion traces.
DPAWS 9.0 Takes Less Know-how
Earlier, identifying and testing chip security flaws required highly trained and specialized technicians. Those operations required considerable skill, and they were largely performed manually, taking hours and days in some cases.
Conversely, DPAWS 9.0 allows less-experienced technicians to run the testing. To operate DPAWS 9.0, personnel with a basic working knowledge of this system can run these tests. This ease of operation and point and click alleviates a company from relying on only a few highly specialized technical personnel. Rather, engineers of virtually any discipline can easily become adept at operating DPAWS 9.0 and be available as backups in case they’re needed.

Leave a Reply