Learn everything you need to know about MACsec, also known as Media Access Control Security.
For end-to-end security of data, it needs to be secured when at rest (processed or stored in a device) and when in motion (communicated between connected devices). For data at rest, a hardware root of trust anchored in silicon provides the foundation upon which all data security is built. Similarly, for data in motion, security anchored in hardware at the foundational communication layer provides that basis of trust, and that’s where MACsec enters the picture.
In this article:
How do you protect data in motion?
The answer: network security protocols.
There are three common network security protocol standards:
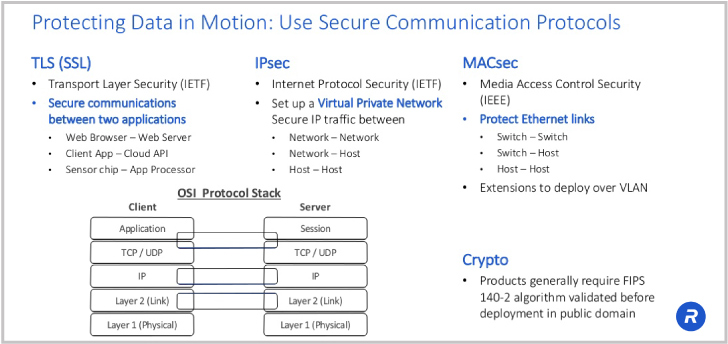
- At the top of the OSI networking model, there is application-layer communication security with TLS. TLS is an improved version of SSL (Secure Sockets Layer) and stands for Transport Layer Security. TLS protects web browsers, client applications, and all the applications’ communications to cloud services.
- Lower down the stack at layer 3 there is IP security or IPsec. IPsec is typically used to protect networks, so if you’re connecting to your corporate network via a VPN, security is provided by IPsec.
- Finally, at Layer 2 there is MACsec which is used to protect network-to-network or device-to-network connections.
Watch webinar: Protecting Data in Motion with MACsec
What’s needed in a network security protocol?
Security protocols have to work within the performance context of the network. As such, bandwidth, latency, prioritization and the diversity in the network have to be considered.
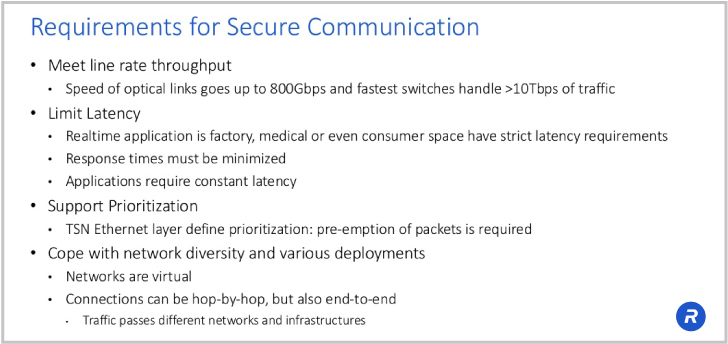 Today line rates are rising rapidly driven by a vast proliferation of applications. People are streaming up to 4K video. Cameras are transmitting data to the cloud. The number of IoT devices is increasing into the billions. Network speeds of 400G are now common in the heart of the global network with 800G links now being deployed. Security protocols should operate at line rate in order to support the performance of the network.
Today line rates are rising rapidly driven by a vast proliferation of applications. People are streaming up to 4K video. Cameras are transmitting data to the cloud. The number of IoT devices is increasing into the billions. Network speeds of 400G are now common in the heart of the global network with 800G links now being deployed. Security protocols should operate at line rate in order to support the performance of the network.
A second important consideration is latency. If a security protocol increases overhead and affects network latency, that can have a negative impact on application performance. Real-time applications such as video conferencing are extremely latency sensitive.
A third important consideration is support for prioritization. Not all packets are equally important and if you’re watching a long video stream with large packets, a hiccup is not that problematic. The packets for a remote surgery, however, needs to be given the highest priority.
Finally, security protocols need to deal with diversity in the network. Not all protocols operate within all different use cases. With the diversity of the various networks, it’s very important that implementations are generic. One connection can be hop-by-hop between two switches, but connections can also be over public networks with vastly differing types and generations of equipment.
Having all these details in mind, let’s dive into MACsec.
What is MACsec security?
MACsec or Media Access Control security provides security of data between Ethernet-connected devices.
The MACsec protocol is defined by IEEE standard 802.1AE. Originally, Media Access Control Security secured the link between two physically connected devices, but in its current form can secure data communications between two devices regardless of the number of intervening devices or networks.
How does MACsec work?
When MACsec is enabled, a bi-directional secure link is established after an exchange and verification of security keys between the two connected devices. A combination of data integrity checks and encryption is used to safeguard the transmitted data.
The sending device appends a header and tail to all Ethernet frames to be sent, and encrypts the data payload within the frame. The receiving device checks the header and tail for integrity. If the check fails, the traffic is dropped. On a successful check, the frame is decrypted.
Don’t have time to read the whole article right now?
No worries. Let us send you a copy of a related white paper so you can read it when it’s convenient for you. Access it here »
MACsec: the foundation for network security
One of the most compelling cases for MACsec is that it provides Layer 2 (OSI data link layer) security allowing it to safeguard network communications against a range of attacks including denial of service, intrusion, man-in-the-middle and eavesdropping.
These attacks exploit Layer 2 vulnerabilities and often cannot be detected or prevented by higher layer security protocols. In this way, MACsec provides the foundational security on which a network security architecture can be built.
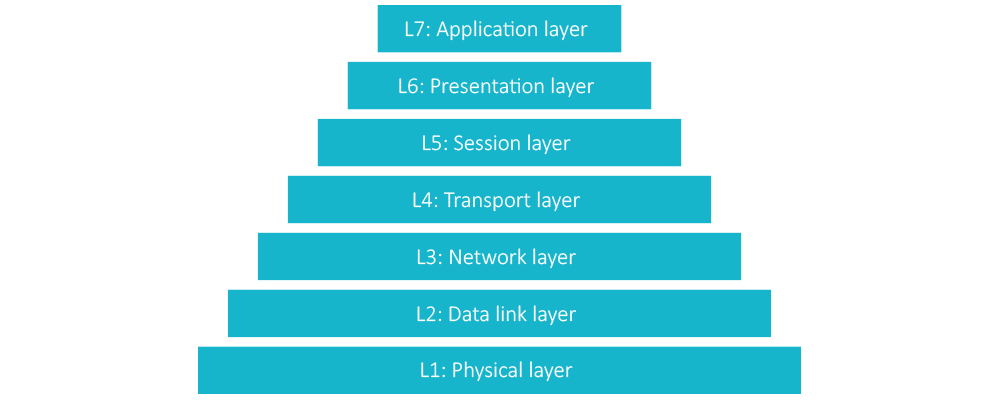
The OSI model partitions a communication system into seven layers. Each of these abstraction layers serves the layer above and is served by the layer below.
From a security standpoint, each layer can secure its activities and those above it, but depends on the security of the layers below. Since Layer 2 is where communication begins, security here establishes the foundation for security for the entire network stack.
The advantages of MACsec
In addition to providing foundational level network security, MACsec offers many other advantages:
1. Scalability: MACsec is very scalable and it can be deployed in different ways compared to other cryptographic protocols such as TLS and IPsec. The algorithm used within the MACsec protocol is very suitable for high network speeds. It also has low latency, because the cryptographic algorithm employed allows starting of processing of the head of the packet without knowing the tail of the packet.
2. No software intervention: The MACsec protocol can be implemented fully in hardware without any software intervention. IPsec, TLS, or any other protocol require interaction of software.
3. Full speed operation: Another compelling advantage of MACsec is that it operates at line rate. Speed is critical as networks and data centers need all the bandwidth they can get to handle the deluge of data traffic. Line rate operation means networks can get the robust Layer 2 security of Media Access Control Security with no sacrifice in performance.
4. Other features and benefits:
Going deeper, here is what else MACsec offers:
- Device-to-device security – MACsec establishes secure transfer of data between two devices regardless of the intervening devices or network. This has allowed MACsec to be used in LANs, MANs and WANs to secure data communication.
- Connectionless data integrity – Unauthorized changes to data cannot be made without being detected. Each MAC frame carries a separate integrity verification code, hence the term connectionless.
- Data origin authenticity – A received MAC frame is guaranteed to have been sent by the authenticated device.
- Confidentiality – The data payload of each MAC frame is encrypted to prevent it from being eavesdropped by unauthorized parties.
- Replay protection – MAC frames copied from the network by an attacker cannot be resent into the network without being detected. In special configurations, with the possibility of frame reordering within a network, limited replay can be permitted.
- Bounded receive delay – MAC frames cannot be intercepted by a man-in-the-middle attack and delayed by more than a few seconds without being detected
Where is MACsec used?
Ethernet has become the ubiquitous communication solution from the desktop to the carrier network.
A growing torrent of network traffic has driven rapid advancements in the performance of Ethernet with 800G Ethernet representing the latest milestone in the evolution of the standard.
With MACsec as the foundational security technology for safeguarding data in motion across Ethernet networks, the use cases are many:
- WAN/MAN routers
- Data center routers and switches
- Server, storage and top-of-rack switches
- LAN switches
- Secure endpoints such as security cameras and industrial robots
Here’s an example:
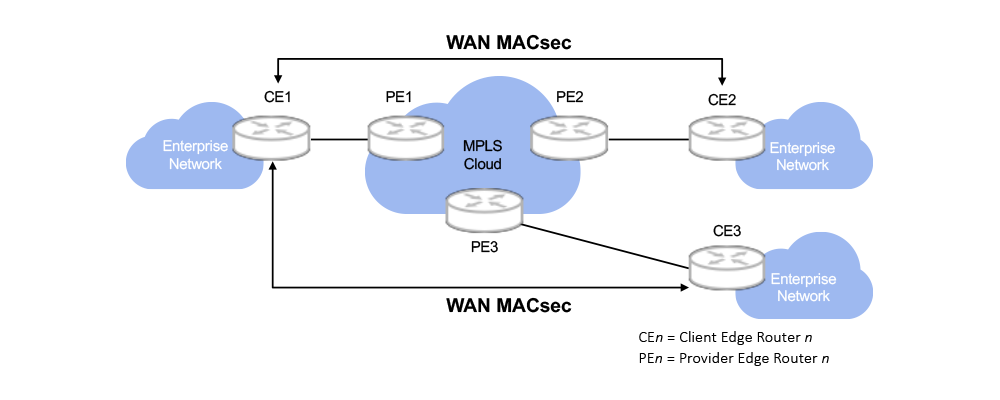
Imagine a global enterprise with multiple enterprise networks, here we show three (the enterprise network clouds).
At the edge of each enterprise network is an edge router (CEn). Each CE connects to a service provider edge router (PEn). The MPLS (Multi-protocol Label Switching used for speed and to guarantee QoS levels) service provider network, which may span many routers, optical transport networks, etc., links the PEs.
MACsec can be used to securely connect two CEs.
The service provider network passes the traffic using “in the clear” routing information in the header. But the key authentication, integrity checks and encryption of MACsec are still enforced just as if CE1 and CE2 were physically connected. And this scales to any number of devices, so we could link to tens or hundreds of other MAC-sec enabled CEs.
Now, imagine there is an industrial robot at the far end of Enterprise Network 1 (CE1’s cloud), and there is a server running an AI inference application in Enterprise Network 2 (CE2’s cloud).
We could securely connect these two devices to switches using MACsec, and those switches to the CEs providing end-to-end security with Media Access Control Security.
Device-level use cases
Let’s turn now to specific device-level use cases for MACsec.
1. Use case: securing 800G multi-port PHY
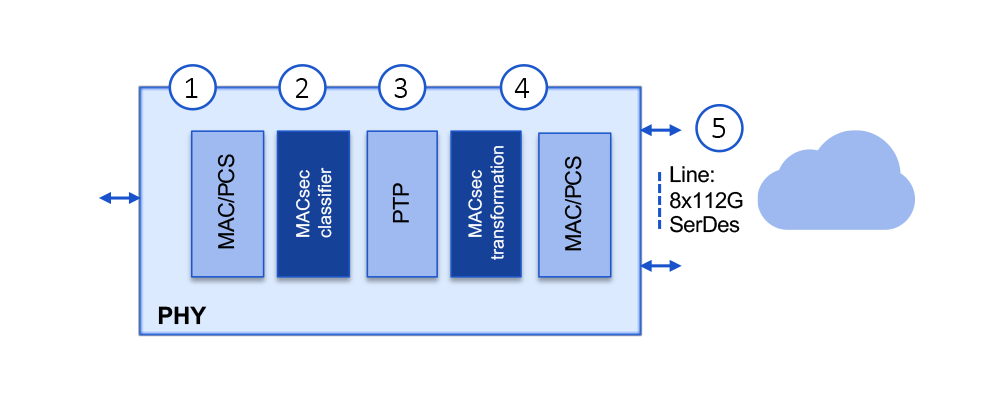
In our first use case, we want to provide communication security for an 800G Multi-port PHY.
We need line-rate encryption of the output which could be one 800G channel or 8 parallel 100G channels with aggregate bandwidth of 800 Gbps. The solution is provided by our multi-port MACsec engine consisting of MACsec classifier and MACsec transformation cores that are incorporated in the PHY transceiver chip. The system would work like this for outbound (transmit) data:
- Time-sliced (TDM) parallel data streams are received by the PHY transceiver chip
- Packet headers are classified
- Data rate is controlled based on the classification and timestamping performed per the precision time protocol (PTP)
- Security implemented (transform packet) with option of constant latency or predictable latency
- Encrypted and authenticated data stream transmitted at line rate under all conditions
In the 800G PHY use case, we assumed all traffic would be MACsec secured. What about the use case for a switch where we have differing security needs depending on the port. We’ll take a look at that use case next.
2. Use case: securing terabit switch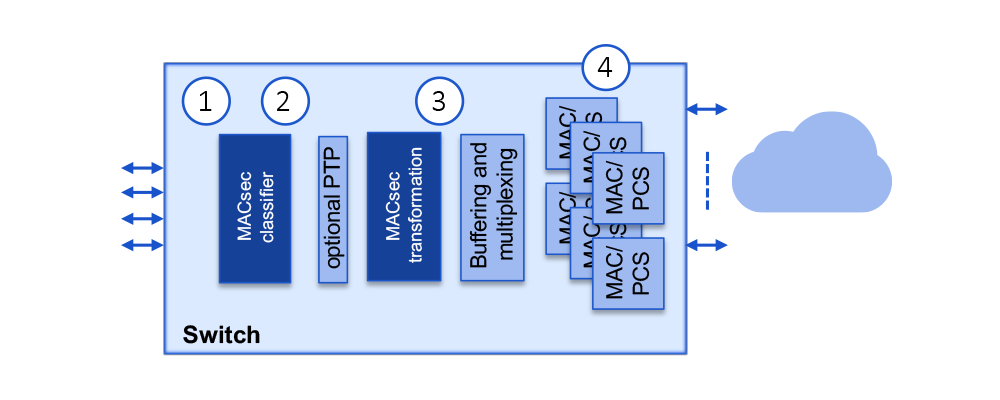
In our terabit switch, a subset of traffic requires MACsec security.
The solution is a multi-port MACsec engine implemented in the switch ASIC. The MACsec engine is capable of servicing a flexible number of ports with aggregate throughput of up to 800 Gbps. Here’s how that would work:
- TDM data is received
- Packet headers classified for all ports that require security
- Allow deep packet inspection for MACsec EoMPLS
- Support various proprietary schemas if required
- Provide optional support of switch classifier inputs
- Add security (transform packet) with encryption of the data payload
- Stream out encrypted and authenticated data at line rate under all conditions to all protected ports
Keep on reading: Rambus Launches 800G MACsec Multi-Channel Engine
Solutions and next steps
Rambus has security IP solutions for all the protocols mentioned: TLS, IPsec, and of course, MACsec.
MACsec solution: For networking SoC and ASIC designers, Rambus offers an 800G Multi-Channel MACsec Protocol Engine comprised of Transform and Classifier cores. It can support up to 64 channels with aggregate bandwidth of 800 Gbps providing tremendous design flexibility. It is supported with a widely-adopted MACsec Toolkit and a Driver Development Kit.
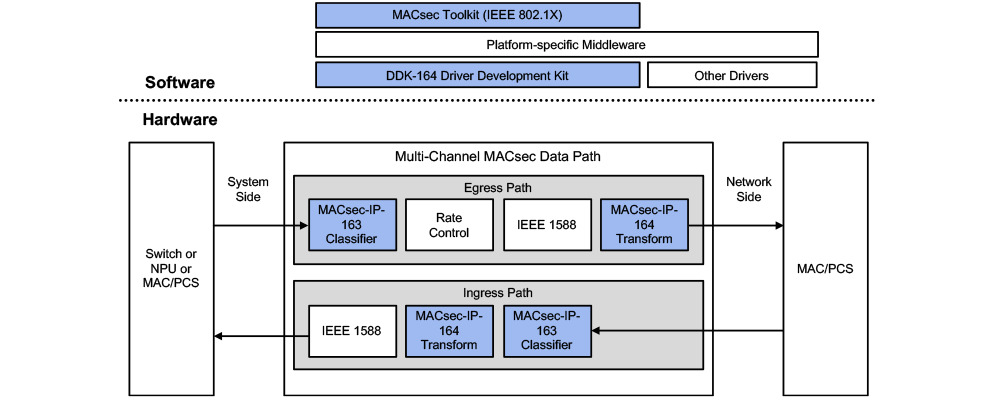
800G Multi-Channel MACsec Protocol Engine
With the Rambus 800G MACsec Protocol Engine, designers get the benefits of robust Layer 2 security with line-rate performance. It can be easily integrated into networking chips and is backed with supports and services from the world-class Media Access Control Security experts at Rambus.
With the industry’s broadest security portfolio, we are able as a company to offer solutions for all your security needs, whether that’s for client devices, networking or anything in between.
Need more details? Contact us here and request a meeting with one of our dedicated sales specialists.
Explore more primers:
– Hardware root of trust: All you need to know
– PCI Express 5 vs. 4: What’s New?
– Side-channel attacks: explained
– DDR5 vs DDR4 – All the Design Challenges & Advantages
– Compute express link: All you need to know
– The Ultimate Guide to HBM2E Implementation & Selection

Leave a Reply