Defining the IIoT
Objects, sensors, actuators and controllers that were once designed for stand-alone operation are now increasingly connected by means of intelligent software and networks – forming the basis of the Industrial Internet of Things (IIoT). To be sure, GE defines the IIoT as “a network of a multitude of devices connected by communications technologies that results in systems that can monitor, collect, exchange, analyze, and deliver valuable new insights.”
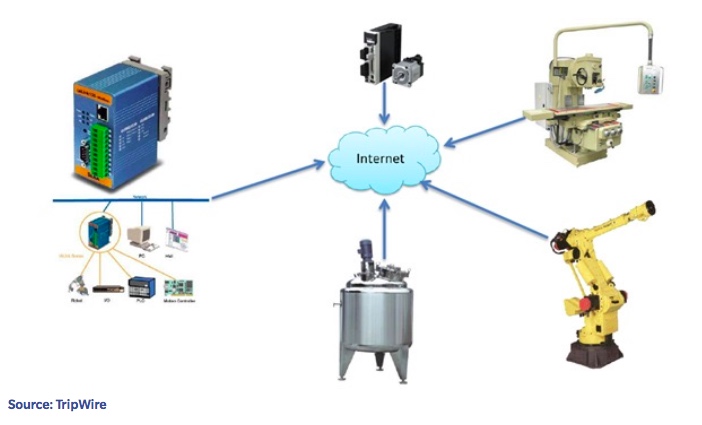
An industrial robot is typically equipped with multiple sensors. One or more of these sensors may link to actuators that, in turn, control the robot’s movement. Sensors, actuators, and other components often connect independently to an IP network with a centralized server that governs overall control of the robot.
The IIoT as a target
The IIoT spans multiple industries including power and energy, oil and gas, manufacturing, chemical plants, healthcare, and aviation. As expected, the widespread global deployment of IIoT infrastructure has provided an attractive platform for targeted attacks by cyber criminals and other unscrupulous operators. For example, in 2016 malicious attackers digitally infiltrated the Kemuri Water Company (Note: real company name withheld by Verizon) using SQL injection and phishing techniques.
According to various reports, the hack exposed login credentials of KWC’s aging AS/400 based operational control system stored on the front-end web server. This system – connected to the internet – managed programmable logic controllers (PLCs) that regulated the valves and ducts controlling the flow of water and chemicals. As Gartner’s Susan Moore confirms, the attackers managed to alter the levels of chemicals used to treat tap water, threatening the health and safety of affected citizens.
Cyber-attacks may be motivated by a number of factors such as corporate espionage or sabotage, financial gain (ransomware), political activism, or personal grievances. It is important to emphasize that an attack executed by a state or terrorist group against a sensitive IIoT target could potentially have a wider environmental impact than initially anticipated.
IIoT cyber threats
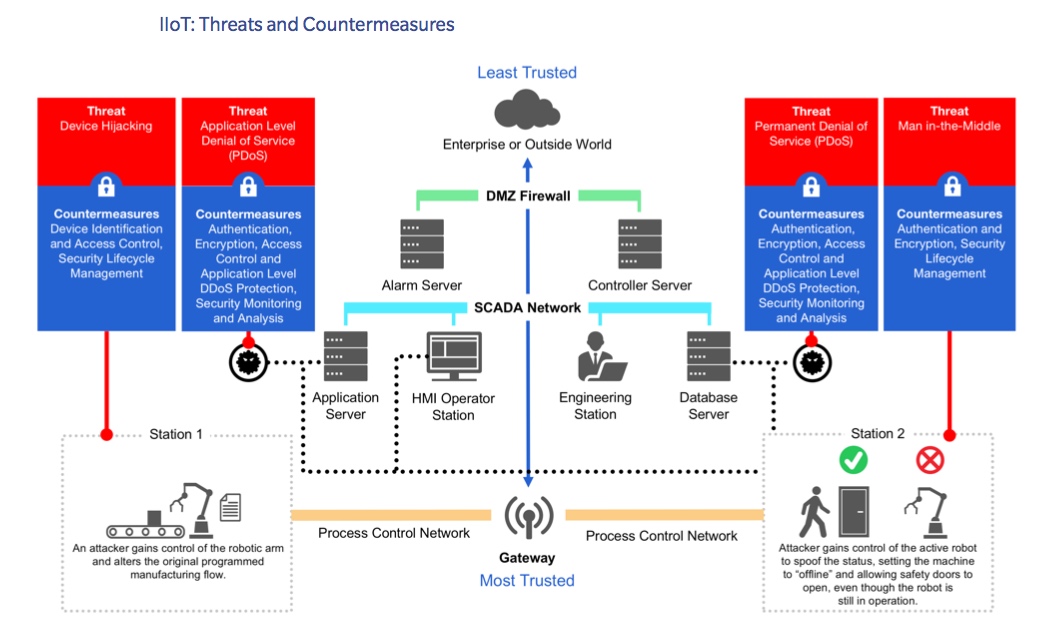
Cyber threats are primarily aimed at industrial control systems (ICS) such as distributed control systems (DCS); programmable logic controllers (PLC); supervisory control and data acquisition (SCADA) systems; and human machine interfaces (HMI). Some examples of vulnerabilities include unsecured remote access, device hijacking, man in-the middle attack, inadequate firewalls and a lack of network segmentation.
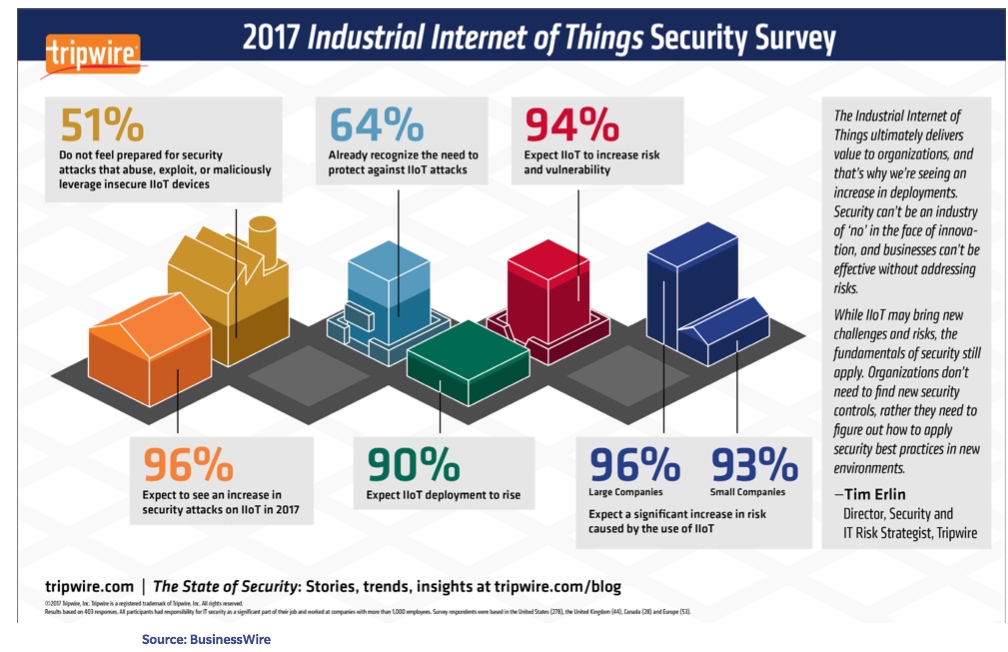
Although malicious operators routinely target various segments of the manufacturing industry, research data suggests that energy organizations are more prone to such attacks, which have steadily become more sophisticated over the years. Indeed, at least 75% of energy companies have reported one or more successful attacks in the past year.
There is a clear need for IIoT infrastructure to be protected by a comprehensive security solution (device-to-cloud) that does not disrupt operations, service reliability or profitability. A practical and simple, yet secure solution that can be easily and widely adopted by IIoT operators and their respective services is more effective than a ‘super solution’ that fails to gain serious traction. Such a solution should include a range of capabilities, including: firmware integrity and secure boot; mutual authentication; secure communication (end-to-end encryption); security monitoring and analysis; and security lifecycle management.
Rambus CryptoManager IoT Security Service for the IIoT
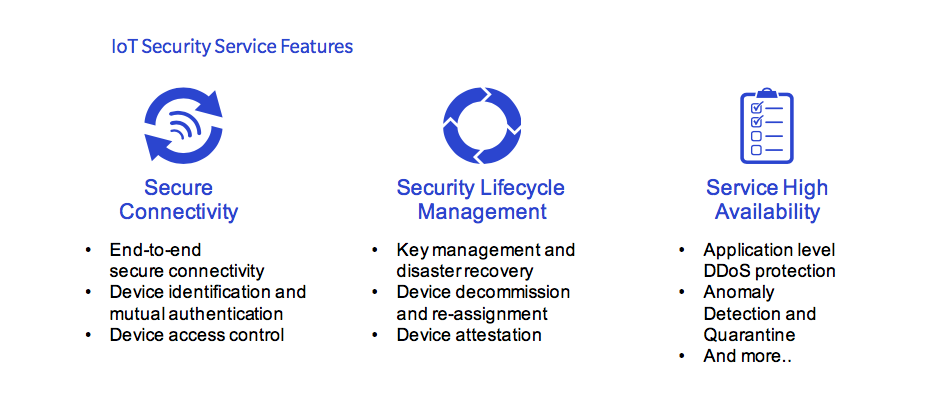
The Rambus CryptoManager IoT Security Service is a turnkey security solution for IIoT OEMs and service providers. Our one-stop-shop solution provides seamless device-to-cloud secure connectivity, device lifecycle management, and advanced device monitoring capabilities to protect service high-availability — while helping to mitigate a variety of attacks such as distributed denial of service (DDoS).
The CryptoManager IoT Security Service is comprised of a client software development kit (SDK) that is pre-integrated with the chipset SDK and IoT PaaS provider to enable an easy to deploy security solution. When a supported device is first powered up and connected to the internet, it is automatically identified and authenticated by our solution. More specifically, the Rambus CryptoManager IoT Security Service both authenticates and provisions an IoT device by leveraging its root-of-trust. This creates a trusted connection, allowing an IoT device to securely transmit data to its IoT service. Concurrently, the Rambus CryptoManager IoT Security Service enables service providers to securely manage devices throughout their respective lifecycles.
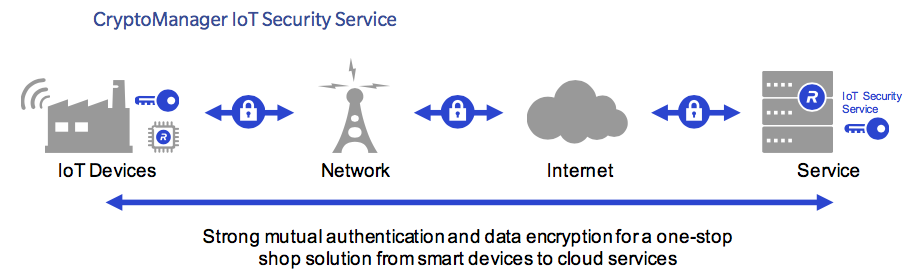
Our IoT Security Service significantly reduces the risk of application layer DDoS attacks and related service outages – and automatically updates device credentials after the resolution of security incidents. The Rambus CryptoManager IoT Security Service also facilitates periodic updates to ensure minimal service disruption, thereby preventing the need for costly manual replacement in the field. Additionally, the IoT Security Service reduces the risk of devices being hijacked, copied, re-purposed, or even disabled by leveraging strong authentication between the device and service.
Interested in learning more about Rambus’ IoT Security Service for the Industrial Internet of Things (IIoT?) You can download our white paper below.

