All physical electronic systems routinely leak information about the internal process of computing via fluctuating levels of power consumption and electro-magnetic emissions. Much like traditional safecracking, an electronic side-channel attack (SCA) eschews a brute force approach to extracting keys and other secret information from a device or system. As such, an SCA conducted against electronic devices and systems are non-intrusive, relatively simple and inexpensive to execute. SCAs comprise a wide range of techniques including Differential Power Analysis (DPA), Simple Power Analysis (SPA), Simple Electromagnetic Analysis, Differential Electromagnetic Analysis, Correlation Power Analysis and Correlation Electromagnetic Analysis.
Have you read our primer?
– Side-channel attacks: explained
Attacking deep neural networks
Recently, a team of white hat researchers created a side-channel technique specifically designed to reveal the internal structure and parameters of deep neural network (DNN) computer vision models. As the researchers note in a paper published on arXiv, studies indicate that DNNs are vulnerable to adversarial attacks, which can be either white-box or black-box.
“During the computation process of the DNNs, the side-channel information shows strong correlations to the network structure and its parameters,” the researchers explain. “We envision that SCA can be used for embedded AI devices and reveal their network architectures and even the corresponding parameters. In other words, we intend to use SCA to open the black-box of DNNs, which can facilitate adversarial attacks by transforming a black-box attack to an at least partial white-box, or gray-box, attack.”
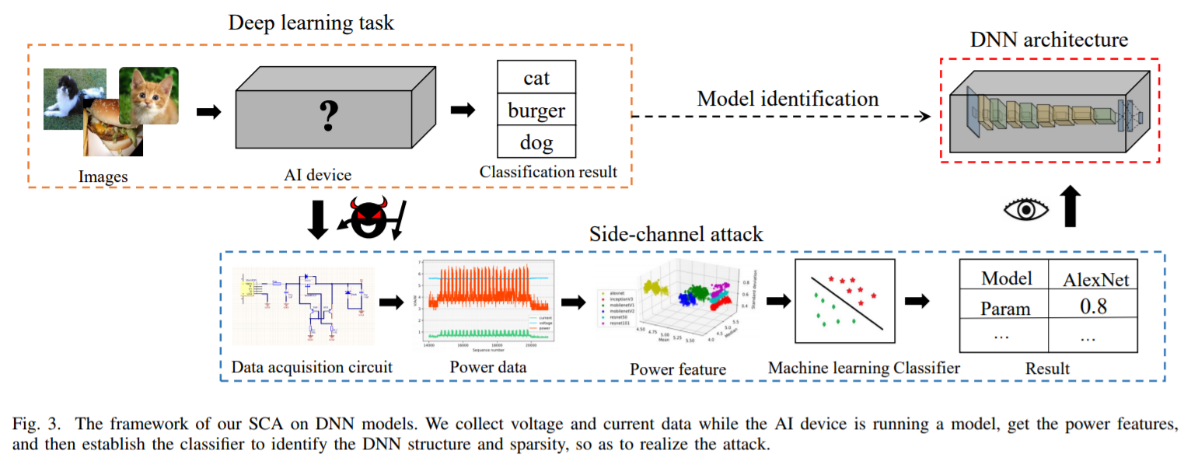
Image Credit: Yun Xiang, Zhuangzhi Chen, Zuohui Chen, Zebin Fang, Haiyang Hao, Jinyin Chen, Yi Liu, Member, IEEE, Zhefu Wu, Qi Xuan, Member, IEEE and Xiaoniu Yang (via arXiv)
To execute their SCA against a DNN, the researchers designed a Raspberry-Pi based platform to derive the power signature of embedded AI devices. The team then utilized machine learning algorithms to identify specific DNN architectures. As the researchers note, the Raspberry Pi is an ARM cortex-based system that shares the common architecture of many existing devices. As such, the experiments performed on the Pi can be easily applied to similar systems.
“One critical observation is that different components [convolutional layers, pooling layers, fully connected layers and activation function] require different computational cost,” the researchers state. “Therefore, different architectures have different power consumption patterns, which makes DNN architectures vulnerable to SCAs. In general, our technique can identify both the architecture and model parameters with quite high accuracy, indicating that we should pay strong attention to the security problem of many AI applications.”
In the future, the white hat security team plans to improve its experimental platform by analyzing additional DNN architectures and parameters with advanced machine learning algorithms that more precisely identify DNN models.
SCA resistance and countermeasures
To protect the internal structure and parameters of deep neural networks (DNNs), we recommend implementing an effective layer of side-channel countermeasures via hardware (DPA resistant cores), software (DPA resistant software libraries) or both. Countermeasures – including leakage reduction, noise introduction, obfuscation and the incorporation of randomness – are critical to ensuring the protection of sensitive keys and data. It should be noted that stand-alone noise introduction is incapable of sufficiently masking side-channel emissions. Indeed, DPA conducted against a device can effectively bypass stand-alone noise countermeasures, ultimately allowing the signal to be isolated.

After layered countermeasures have been implemented, systems should be carefully evaluated with a Test Vector Leakage Assessment (TVLA) platform such as the Rambus DPA Workstation (DPAWS) to confirm the cessation of sensitive side-channel leakage. More specifically, DPAWS measures a range of side-channel attacks across a wide spectrum of devices and platforms. DPAWS also provides users with a highly intuitive UI paired with enhanced data visualization that creates an integrated, project-centric analytic environment specifically designed to optimize the efficiency of side-channel analysis.
Both flexible and scalable, DPAWS supports multiple side-channel sensors, device protocols and form factors, with out-of-the-box support for SASEBO and additional third-party hardware. DPAWS also easily integrates with a wide range of industry tools including Matlab, Python and other scripting languages. Moreover, the Rambus DPA Workstation supports full cipher coverage (AES, RSA, ECC, DES and SHA), large dataset handling, as well as high-speed collection and analysis of billions of traces. Source code is also available to facilitate increased flexibility.
Interested in learning more about protecting systems from side-channel attacks?

Leave a Reply