U.S. Sens. Mark R. Warner (D-VA) and Cory Gardner (R-CO), co-chairs of the Senate Cybersecurity Caucus, along with Sens. Ron Wyden (D-OR) and Steve Daines (R-MT), have introduced bipartisan legislation to bolster the security of Internet-connected devices.
Specifically, the Internet of Things (IoT) Cybersecurity Improvement Act of 2017 would require that devices purchased by the U.S. government meet certain minimum security requirements.

“Under the terms of the bill, vendors who supply the U.S. government with IoT devices would have to ensure that their devices are patchable, do not include hard-coded passwords that can’t be changed and are free of known security vulnerabilities, among other basic requirements,” the above-mentioned senators stated in an official press release. “The bill […] also promotes security research by encouraging the adoption of coordinated vulnerability disclosure policies by federal contractors and providing legal protections to security researchers abiding by those policies.”
Commenting on the Cybersecurity Improvement Act, Bruce Schneier, Fellow and Lecturer at Harvard Kennedy School of Government, observed that the proliferation of insecure Internet-connected devices presents an enormous security challenge.
“The risks are no longer solely about data; they affect flesh and steel. The market is not going to provide security on its own, because there is no incentive for buyers or sellers to act in anything but their self-interests,” said Schneier. “I applaud Senator Warner and his cosponsors for nudging the market in the right direction by establishing thorough, yet flexible, security requirements for connected devices purchased by the government.”
Unsurprisingly, the Cybersecurity Improvement Act was introduced shortly after the United States Government Accountability Office published a report that recommends “enhanced assessments and guidance” to address IoT security risks in the Department of Defense (DoD).
According to the report, IoT devices pose numerous security challenges that need to be addressed, both in specific instances and as part of a holistic approach to risk management in the information age.
“The Department of Defense (DoD) has identified numerous security risks with IoT devices and conducted some assessments that examined such security risks, such as infrastructure-related and intelligence assessments. Risks with IoT devices can generally be divided into risks with the devices themselves and risks with how they are used,” the DoD stated.
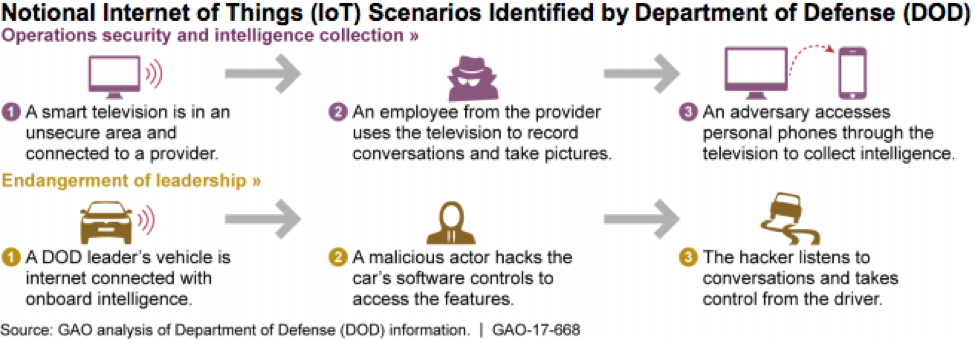
“For example, risks with the devices include limited encryption and a limited ability to patch or upgrade devices. Risks with how they are used—operational risks—include insider threats and unauthorized communication of information to third parties. [The] DoD has [also] developed IoT threat scenarios involving intelligence collection and the endangerment of senior DOD leadership—scenarios that incorporate IoT security risks.”
The above-mentioned Government Accounting Office IoT-DoD document joins a slew of recent federal reports, recommendations and warnings about the importance of securing the Internet of Things. These include an FBI PSA expressing concern over IoT-connected toys, a GAO paper outlining the risks of an unsecured IoT, a threat assessment that explores the role of IoT devices in DDoS attacks and a U.S. Department of Homeland Security (DHS) report which emphasizes the importance of implementing security at the design phase.

