Side-channel attacks conducted against electronic systems are relatively simple and inexpensive to execute. An attacker does not need to know specific implementation details of the cryptographic device to perform these attacks and extract keys. As all physical electronic systems routinely leak information, effective side-channel countermeasures such as Rambus’ DPA Resistant Hardware Cores (DPARC) or DPA Software Library (DPASL) should be implemented at the design stage to ensure protection of sensitive keys and data. After the implementation of hardware or software countermeasures, systems should be carefully evaluated with a Test Vector Leakage Assessment (TVLA) platform such as the Rambus DPA Workstation (DPAWS) to confirm the cessation of sensitive side-channel leakage.
Security IP
CryptoManager Infrastructure for Semiconductor Manufacturing Data Brief
Securing the Industrial Internet of Things
Objects, sensors, actuators and controllers that were once designed for stand-alone operation are now increasingly connected by means of intelligent software and networks – forming the basis of the Industrial Internet of Things (IIoT). To be sure, GE defines the IIoT as “a network of a multitude of devices connected by communications technologies that results in systems that can monitor, collect, exchange, analyze, and deliver valuable new insights.”
IIoT infrastructure, as well as the data it generates, must be protected against a wide range of cyber threats. Vulnerable devices can be hijacked and even physically disabled, while unencrypted or unverified data transmissions can be intercepted, leaked or spoofed. A leak or deliberate falsification of sensitive data could cause a halt in factory operations, electrical blackouts or malfunctioning water treatment centers.
Despite the real-world risks, IIoT operators are understandably concerned that implementation of a comprehensive security solution could pose integration challenges and incur additional costs. As such, the most effective security solution is one that does not negatively impact operations, reliability or profitability. Put simply, a practical, simple and secure solution that can be easily and widely adopted by IIoT OEMs and service providers is far more effective than a ‘super solution’ with only limited adoption.
The Rambus CryptoManager IoT Security Service is a turnkey security solution for IIoT OEMs and service providers. As we highlight in our white paper, our one-stop-shop solution provides seamless device-to-cloud secure connectivity, device lifecycle management, and advanced device monitoring capabilities to protect service high-availability and help mitigate a variety of attacks, including distributed denial of service (DDoS).
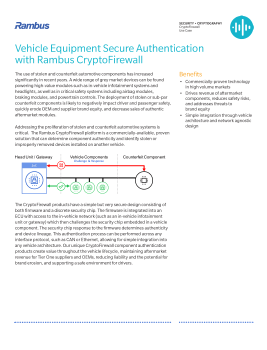
Vehicle Equipment Secure Authentication with Rambus CryptoFirewall
Hardware Security Modules with CryptoManager
Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). An attacker does not need to know specific implementation details of the cryptographic device to perform these attacks and extract keys. As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.