AES-IP-38 AES XTS/GCM Accelerators
Home > Security IP > Crypto Accelerator Cores > AES-IP-38
The AES-IP-38 (EIP-38) is IP for accelerating the AES symmetric cipher algorithm supporting GCM or XTS modes at extreme speeds up to 100 Gbps+ @ 850 MHz. Designed for fast integration, fast key switching and high performance, the AES-IP-38 accelerator provides a reliable and cost-effective embedded IP solution that is easy to integrate into high speed crypto pipelines. The IP supports Cipher Text Stealing (CTS) in combination with AES-XTS.
AES XTS/GCM family of high speed accelerators.
Available in 12 configurations / performance grades.
Full key and data path integrity option.
How the AES-IP-38 AES XTS/GCM Accelerators work
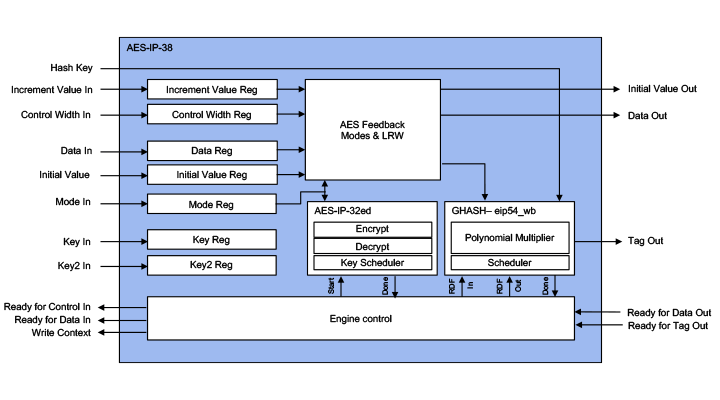
The AES-IP-38 is a family of the cryptographic library elements in the Rambus hardware IP library (formerly of Inside Secure). For example, the AES-IP-38 is the cipher core embedded in all MACSec protocol aware security engines. The accelerators include I/O registers, encryption and decryption cores, and the logic for feedback modes and key scheduling.
Even though the Advanced Encryption Standard (AES) algorithm was designed to allow high-speed implementations, its regular feedback modes such as CBC, CFB, and OFB are not ideal for supporting very high-speed networking applications. The AES-GCM and AES-XTS algorithms do not use these regular AES feedback modes and allow very high-speed encryption and authentication by enabling an implementation to make use of parallelism. Typical uses cases for AES-GCM and AES-XTS are high-speed transmission (virtual private networking) and disk storage (protection of data at rest). For transmission protection, AES-GCM can for instance implement authenticated encryption at the network layer (IPsec) or at the data link layer (IEEE 802.1ae). The AES-GCM (Galois Counter Mode) has, since its publication in 2005, been used in many IPsec and MACsec applications. It is a very efficient algorithm, suitable to achieve very high performances. AES-XTS has been adopted by IEEE P1619 for protection of data at rest. The AES-IP-38 also supports the legacy AES-LRW algorithm. Within the AES-IP-38 product family a range of AES-XTS configurations is available that allows efficient key switching while maintaining throughputs for small sector sizes, ex- and including CTS.
Sustained performance for any object sizes ranges from 6 to 100 Gbps+ depending on the configuration and area. Gate count is between 90K and 650K gates depending on the configuration. Multiple AES-IP-38 cores can be cascaded. Tailored for storage solutions, a dedicated configuration offering full key and data path integrity is available.

Anti-Tampering Technologies
The design of chip anti-tamper protection needs to adapt and scale with rising threats. Adversaries range from high school hackers to well-funded state actors. Given the threats, it’s useful to think about anti-tamper countermeasures as a hierarchy of safeguards that parallel the type, effort and expense of attacks. Watch this webinar to learn the eleven kinds of tampering attacks and their required skills and resources, and countermeasures for each of these attacks.
AES-IP-38 Information
Key benefits:
- Silicon-proven implementation
- Fast and easy to integrate into SoCs
- Flexible layered design
- Complete range of configurations
- World-class technical support
Configuration Flexibility:
- The AES-IP-38 accelerators are available in different configurations, suitable for different applications, and for meeting different gate count and throughput objectives.
- The AES-IP-38 is available in configurations supporting all modes, and dedicated XTS (and ECB) only configurations (EIP-38x-*), which are optimized for XTS operations having very limited overhead switching keys and direction.
Flexible, layered design:
- In order to provide full flexibility and ease of use, the AES/GCM/XTS accelerators feature a layered design. The inner layer, the Engine, provides wide bus interfaces for Mode, Initialization Vector (IVs), Keys, and Data. These wide bus interfaces allow optimal data throughput and extremely fast context switching (that is, use of new Mode, IV, and Key values). Supports Cipher Text Stealing
- For the non-high-speed cores (AES-IP-38b, AES-IP-38b-gcm, and AES-IP-38x-1) an outer layer is available. This outer layer has a 32- bit wide register interface. The input and output buffer registers inside the Shell allow for pipelining – input data and context information can be written and output data can be read while the Engine is performing an AES/GCM/XTS operation at the same time. This way, maximum through put is achieved using a 32-bit register interface.
- The lower speed cores provide customers with the flexibility to be used with or without the Shell. The high-speed cores (AES-IP-38f, AES-IP-38o, AES-IP-38x-IP-5, AES-IP-38x-8, AES-IP-38x-10 and AES-IP-38x-14) must be integrated without the Shell to achieve the optimal performance.
- Customers can also use the Shell logic as a basis for building a customized, width-constrained interface.
Data Integrity Protection:
- On request, the AES-XTS only configurations are available with Data Integrity protection of the data path. All key and data inputs and outputs are extended with a parity bit per byte. The internal data path is extended to protect these vectors against single bit faults.
Features:
- Wide bus interface
- Basic AES encrypt and decrypt operations
- Key sizes: 128, 192 and 256 bits
- Key scheduling in hardware, allowing key, key size and direction changes every 13/15/17 clocks with zero impact on throughput
- Hardware reverse (decrypt) key generation
- Non-feedback modes: ECB and CTR
- Feedback modes: CBC, OFB (128 bit), CFB (1-, 8- and 128-bit)
- AES-LRW with CTS1 (D5)
- AES-XTS with CTS1 (D18)
- AES-GCM (using AES-CTR mode and GHASH)
- Basic GHASH operation (selecting no encryption)
- Fully synchronous design
- (Multiple) High-speed versions (encrypt only, en-/decrypt and XTS only)
- XTS only configurations embed a dedicated CTS AES core allowing CTS to be applied every 10/12/14 clocks with zero impact on throughput
- Optional data integrity protection
Alternatives:
- AES-IP-32 AES ECB accelerators
- AES-IP-36 AES ECB/CBC/CTR accelerators
- AES-IP-37 AES Key Wrap accelerators
- AES-IP-38 AES XTS/GCM accelerators
- AES-IP-39 AES ECB/CBC/CTR/CCM/GCM accelerator

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.
Resources
Videos