AES-IP-61 / EIP-61 High speed low latency AES-GCM pipeline, 100Gbps
Home > Security IP > Crypto Accelerator Cores > AES-IP-61
The AES-IP-61 (EIP-61) is IP for accelerating AES-GCM based cryptographic solutions. Designed for easy integration and very high performance the AES-IP-61 crypto accelerator provide a reliable and cost-effective embedded IP solution that is easy to integrate into high-speed processing pipelines.
High speed, low latency AES-GCM pipeline
100Gbps, separate AES-CTR and GHash pipelines
Fast key switching, low latency
How the AES-IP-61 works
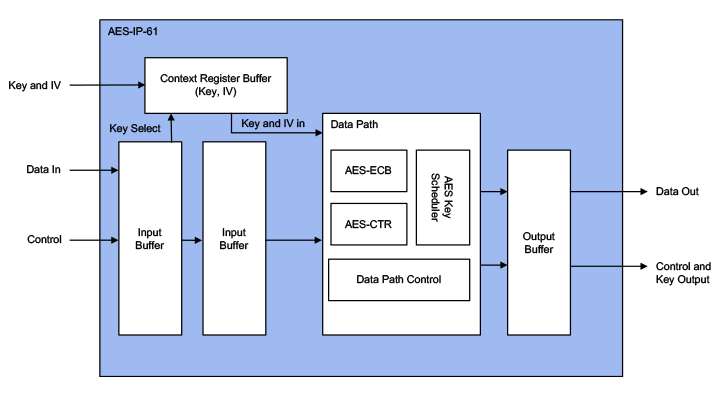
The AES-IP-61 (EIP-61) implements the AES-GCM function with two distinct data paths: one (the AES-IP-61mc) for the AES-CTR cipher mode of the GCM algorithm and one (the AES-IP-61mg) for the GHash mode of the GCM algorithm. The AES-IP-61 is an extreme high performance implementation comprising of 28 parallel AES cipher cores offering performance over 100Gbps @525MHz.
The AES-IP-61 is designed to be the cryptographic accelerator in applications needing raw AES-GCM performance for high speed crypto applications.
Sustained performance @525MHz is 134Gbps for the AES-GCM and 119Gpbs for the GHash mode. The area of the cores together is 890K gates.
AES-IP-61 Information
Key benefits:
- Silicon-proven implementation
- Fast and easy to integrate into SoCs
- Flexible layered design
- World-class technical support
The AES-IP-61mc AES-CTR core is able to process 1 data block of 256-bit size per clock cycle when there are less than or equal to 5 key/IV switches in 15 clock cycles. Two clock cycles are required to load one key/IV pair:
- 256-bit data-path using 28 AES cores with 256-bit key size
- Symmetric AES-CTR block cipher encrypt and decrypt operations
- 10-channel encoding with 2 pairs of keys and IV per channel
- Key switching without performance drop (or hit)
- Key scheduling in hardware
- Non-encrypted data bypass per block
- Fake encryption test mode
- Wide bus interface, 128 bit for data, 256 bit for keys
- Fully synchronous design
The AES-IP-61mg, GHASH core is able to process one data block of 256-bit size per clock cycle and the key switch between data blocks does not require any additional clock cycles as long as there are at least six data blocks processed sequentially with the same key and the minimum frame size is eight data blocks. If a frame is being finalized and there are less than seven data blocks processed sequentially, the AES-GMAC core needs one extra clock to finalize the operation:
- 256-bit data-path
- AES-GMAC (using GHASH) with 256-bit key size
- Hash key (H) calculation
- 10-channel encoding with 2 pairs of keys and IV per channel
- Key switching without performance drop (or hit) for both encryption and description
- 64-bit and 128-bit authentication tags over a statically configurable number of 128-bit blocks
- Wide bus interface, 128 bit for data, 256 bit for keys
- Fake authentication test mode
- Memory interface for storing keys, IV, key derivatives and intermediate state

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.
Resources
Videos