TRNG-IP-76 FIPS-Certified True Random Number Generators
Home > Security IP > Crypto Accelerator Cores > TRNG-IP-76 (True Random Number Generator)
The TRNG-IP-76 is a FIPS-compliant and certified IP core for True Random Number Generation (TRNG) with an optional post-processor and several internal self-tests. Designed for easy integration into ASICs and SOCs, the 100% digital standard cell based TRNG-IP-76 provides a reliable and cost-effective embedded IP solution for our customer’s SoCs.
Non-deterministic Random Number Generator, FIPS-140 SP800-90A/B compliant, ESV certified for NRBGs and DRBGs (#E167).
Available as standalone RBG or embedded in the Rambus RT-130, RT-630, RT-660 Root of Trusts
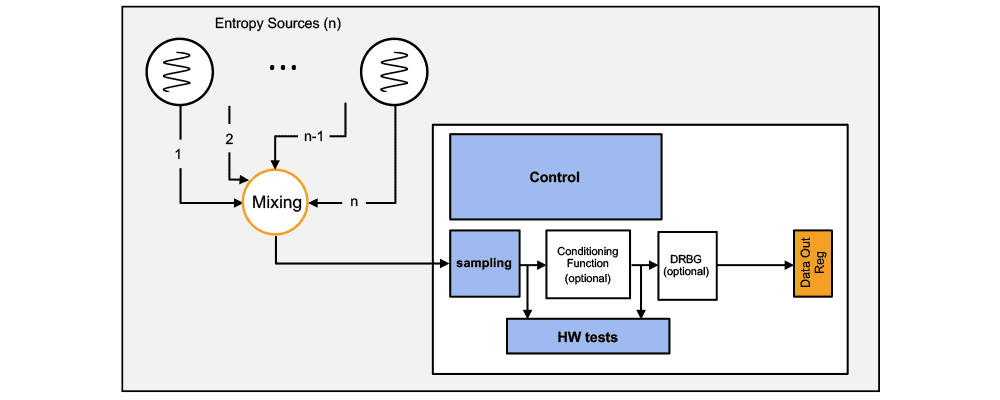
How the TRNG-IP-76 works
TRNGs are typically deployed in semiconductors for securing data communications, electronic transactions, and data storage. They are used for generation of keys, initialization vectors, cookies, and nonces. Additionally, TRNGs can also be used for statistical sampling, communications protocol timers, as well as noise generation.
To provide a hardware-based, nondeterministic noise source the TRNG-IP-76 uses a state of the art reliable free running oscillator (FRO) implementation.. This allows stable operation across very wide process, voltage, and temperature (PVT) ranges, as required for modern process node (45nm and below) semiconductors.
When running asynchronously, the FROs accumulate a timing jitter largely due to shot noise effects. When the signal is sampled, this jitter causes unpredictability of the outcome, thereby providing some entropy. These samples feed a complex, non-linear combinatorial circuit that produces the final TRNG output. This function is referred to as a hardware-implemented Non-deterministic Random Bit Generator (NRBG).
The TRNG-IP-76 is a security aware design:
- Patented test circuits on the oscillators that detect locking to periodic signals.
- Repeating output data detection on NRBG and DRBG (compliant with FIPS-140).
- Hardware-implemented health-tests, including ‘Repetition Count Test’ and ‘Adaptive Proportion Test’ (compliant with SP800-90B).
- Secure random data buffer wipe-after-read and zeroize functions (compliant with FIPS-140).
- Secure reading mode where data is only available on request, for a (configurable) limited time.
- Automatic shutdown on fatal errors.
- Various on-line and off-line integrity and known-answer tests on the Conditioning Function, DRBG and self-test circuits.
The TRNG-IP-76 is compliant with Federal Information Processing Standards (FIPS) Publication 140-3, facilitating system certification. The design is compliant with the latest versions for NIST SP800-90A/B/C. A NIST SP800-90 Deterministic Random Bit Generator (DRBG) is available for the required post processing. The TRNG-IP-76 is ESV certified and is FIPS-approved when integrated into Rambus Root of Trust solutions.
The TRNG-IP-76 is silicon proven, and its flexible, layered design makes it easy to integrate into SoCs. A driver development kit is included.
Features of the TRNG-IP-76
Standard configurations of the TRNG-IP-76 include:
- TRNG-IP-76a-8: base configuration with 8 FROs
- TRNG-IP-76d-8-SHA2: 8 FROs and DRBG
- TRNG-IP-76d-8-BC_DF: 8 FROs, DRBG with BC_DF
All configurations operate with eight Free Running Oscillators (FROs).
In addition to the base configuration, the TRNG-IP-76 offers several configurable options that are described in the NIST specification SP800-90c draft:
- A vetted SHA-2 based conditioning component (SP800-90B), can be embedded in the NRBG. This conditioning component is responsible for increasing the entropy rate to produce full-entropy bit strings used to seed a DRBG.
- A Deterministic Random Bit Generator, based on AES in counter mode, can be added. It can be coupled with a block cipher derivation function in case no conditioning component is present (compliant with SP800-90A).

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.



