CryptoManager Hub (CH-7xx) and CryptoManager Core (CC-7xx) ISO 21434 Automotive-grade
Foundational Crypto Accelerator Cores for Automotive Use Cases
Home > Security IP > Root of Trust Solutions > CryptoManager Hub (CH-7xx) and CryptoManager Core (CC-7xx) ISO 21434 Automotive-grade
The automotive-grade CryptoManager Hub (CMH) and CryptoManager Core (CMC) from Rambus are the next-generation of flexible and configurable cryptographic family of accelerator cores comprised of the CMH CH-7xx and CMC CC-7xx designs and are intended for embedding in customer or Rambus provided HSM security modules.
These cores target automotive power and space-constrained SoCs or FPGAs. The CMC is a collection of efficient symmetric crypto accelerators with state-of-the-art DMA. The CMH embeds a CMC and adds firmware-controlled public key infrastructure capabilities. It supports SESIP-PSA level 2/3 and FIPS 140-3 level 2/3 certifications when integrated into a security module. These automotive-grade configurations offer automotive ISO 21434 compliance and ISO 26262 ASIL-B and ASIL-D safety mechanisms. The ASIL-D configuration offers side-channel attack protection and fault injection attack detection mechanisms.
Featuring a controller-based architecture with dedicated secure memories, the CMH offers a variety of classic asymmetric cryptographic accelerators including RSA, ECC, SM2, TRNG, KDF (Key Derive), as well as Quantum Safe accelerators like ML-DSA, ML-KEM and SLH-DSA. The CMC, without controller, available standalone or embedded in CMH, adds symmetric crypto accelerators for AES, SM4, ChaCha20, SHA-2, SHA-3, SHAKE, SM3 and Poly1305. Ideal for power and space-sensitive automotive applications, central gateways, ADAS/AD compute and AI edge sensors, these accelerators are the most versatile, complete crypto solutions that offer the best balance of size and performance available on the market.
CryptoManager RT-6xx Root of Trust Family: A New Generation of Security Anchored in Hardware

This latest generation CryptoManager RT-6xx Root of Trust IP offers many new features designed to support the security needs of customers today and in the future. These features include Quantum Safe Cryptography, Caliptra Root of Trust for Measurement (RoTM) emulation, DPA and FIA protections, as well as an innovative three-tier architecture that lets customers tailor a Root of Trust solution to their specific requirements.
How the CryptoManager Hub (CH-7xx) and CryptoManager Core (CC-7xx) ISO 21434 Automotive-grade Works
The CMH and CMC are silicon IP cores developed to provide strong and futureproof cryptographic support, enhancing security designs in SoC platforms. The CMC provides highly efficient symmetric cipher, hash and mac accelerators behind an efficient DMA interface. CMC is available as a standalone accelerator engine or embedded in the CMH. CMC comes in many configurations, providing a selection of ciphers AES (all modes), ChaCha20, and SM4 and integrity cores SHA-2 (all modes), SHA-3, SHAKE, HMAC, KMAC, Poly1305, SM3. Implementations offered are standard ASIL-B, or optionally with side channel attack countermeasures, fault injection attack detection mechanisms, and ASIL-D safety mechanisms. Crypto operations on different cores can run concurrently with out-of-order completion capability. Crypto operations can be paused and resumed, with secure save and restore of its internal states. CMC is controlled over an AMBA (AHB or AXI) subordinate interface, where data is transferred over a DMA-based AXI manager interface.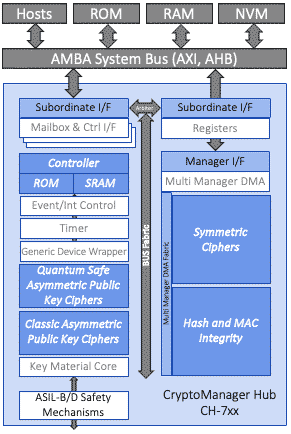
CMH implements a CMC and extends it with a public key infrastructure comprising of a true random number generator, classic and, optionally, Quantum Safe accelerators, orchestrated by an internal controller. Similar to CMC, the same options are offered: standard ASIL-B, and, optionally, DPA and FIA with ASIL-D. A local key store provides local storage of provisioned, derived or generated keys. CMH is also controlled over an Amba (AHB or AXI) subordinate interface, where data is transferred over a DMA-based AXI manager interface. Readily deployable, CMH and CMC are offered in off-the-shelf configurations, allowing a choice tailored to the needs of your application. Configurations differ by cryptographic accelerators contained, protection mechanisms required, and third-party security standard compliance. Rambus can optionally offer dedicated certification support packages to its CMH licensees that provide related certification documentation, test scripts, and dedicated support to achieve FIPS 140-3, SESIP, PSA and ISO 26262/21434 certification with your product embedding the CMH.
Protecting Data and Devices Now and in the Quantum Computing Era

Quantum computing is being pursued across industry, government and academia with tremendous energy and is set to become a reality in the not-so-distant future. Once sufficiently large quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be broken. Many initiatives have been launched throughout the world to develop and deploy new quantum-resistant cryptographic algorithms, known as Post-Quantum Cryptography (PQC).
Solution Offerings
| Feature | CMH | CMC | Description | Details |
| SESIP | √ | √ | Supports systems requiring Level 2/3 | L3 for DPA and FIA configurations |
| PSA | √ | √ | Supports systems requiring Level 2/3 RoT Component | L3 for DPA and FIA configurations |
| FIPS 140-3 | √ | √ | Supports systems requiring FIPS 140-3 | CAVP and CMVP Level 2 |
| ISO 21434, ISO 26262 | √ | √ | Select configurations for automotive | CAL 4 and ASIL-B or ASIL-D |
| Cipher Algorithm Support | √ | √ | AES (all key sizes) Optional: ChaCha20 Optional: SM4 | AES Modes: ECB, CBC, CFB, CTR, GCM, XTS, CMAC, GMAC, CCM, CMAC |
| Hash Algorithms | √ | √ | SHA-2 SHA-3 Optional: SM3 | SHA-2 224-256-384-512 SHA-3 224-256-384-512, SHAKE |
| Message Authentication Code Algorithms | √ | √ | HMAC-SHA-2, HMAC-SHA-3, KMAC-SHA-3 Optional: HMAC-SM3 | SHA-2 224-256-384-512 SHA-3 224-256-384-512 |
| AEAD Algorithms | √ | √ | AES-GCM, AES-GMAC, AES-CCM Optional: ChaCha20/Poly1305 | Modes: GCM, GMAC, CCM |
| Sign/Verify Algorithms | √ | – | ECDSA EdDSA SM2 ML-DSA, SLH-DSA | NIST P-224, P-256, P-384, P-521, Brainpool Ed25519, Ed448 OSCCA Quantum Safe ML-DSA-44/65/87, SLH-DSA (roadmap) |
| Key Agreement Algorithms | √ | – | ECDH EdDH ML-KEM | NIST P-224, P-256, P-384, P-521 Curve25519, Curve448 Quantum Safe ML-KEM-512/768/1024 |
| Key Derive Algorithms | √ | – | NIST SP800-56C NIST SP 800-108r1-upd1 | Two-step KDF AES-CMAC KDF |
| Key Transport Algorithms | √ | – | ECIES RSA Wrap/Unwrap (RSA-OAEP) | 128- and 256-bit strength up to 4096 bits |
| Random Number Generator HW | √ | – | Standard CRNG or AIS-31 NIST SP800-90 compliant TRNG | NIST ENT certificate |
| Crypto Performance | √ | √ | Cipher/Hash Performance | Scalable, ~6 Gbps @1000MHz |
| I/O Bus | √ | √ | AMBA Bus | AXI Manager, AXI/AHB Subordinate |
Complete Documentation
- Integration guides
- Reference manuals
- Programming guides
- FMEDA, DFMEA, DFA, Safety Manual
RTL and FW Package
- Verilog RTL for synthesis and simulation
- Standard EDA tool flow scripts and support files
- Verification test bench and test vectors